There’s a lot of talk about cybersecurity and preventing the bad guys from getting in. But what do you do when they do break through and how quickly can you recover? That’s cyber resilience. Cyber resilience is measured by your ability to continue operations when a cyber incident occurs, and it will.
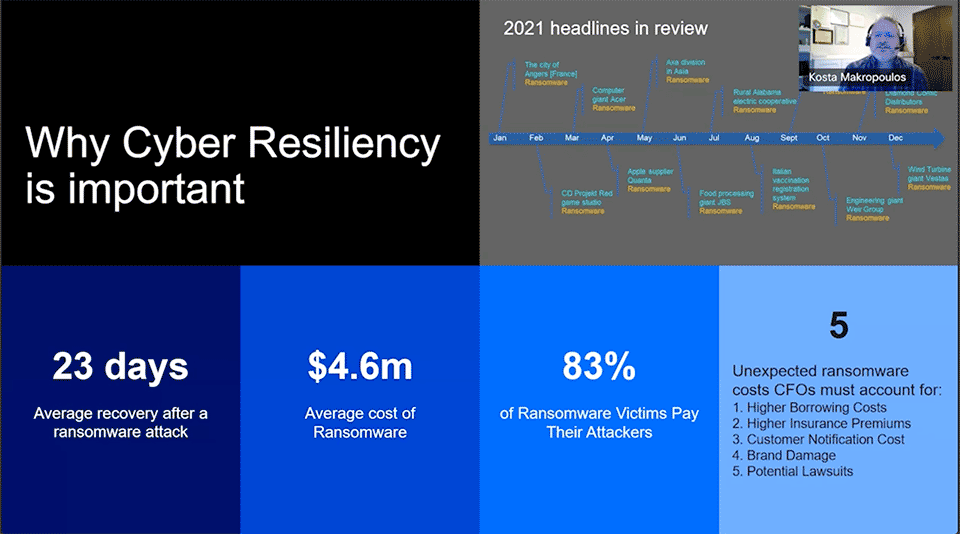
On average it takes 23 days to recover from a ransomware attack. That’s a long time for your business to be vulnerable and unable to fulfill your commitments to customers. And then there’s the unexpected ransomware costs CFOs must account for:
- Higher borrowing costs
- Higher insurance premiums
- Customer notification cost
- Brand damage
- Potential lawsuits
To help ensure your cyber resilience is as strong as it can be, we spoke with Kosta Makropoulos, Consulting IT Specialist at IBM Storage. Kosta shared his insights and best practices to protect your business and operations.
Watch Kosta Makropoulos’s Presentation
Best practices to keep your business operational
According to Kosta, there are 6 key capabilities that can help you manage malicious data breach threats, keep your business operational, and help control costs, including not having to pay the ransomware fine.
- Ensuring applications in the environment have identity and administrative security that can help manage credentials and data access.
- Monitoring and identifying data in the data protection environment for ransomware or malware and taking advantage of some of the latest AI capabilities to determine data pattern anomalies to capture a threat before it can harm all your data.
- Ensuring you have pervasive encryption, starting at the primary storage layer all the way through backups in flight.
- Having multiple layers of backup and utilizing the 3-2-1-1 methodology for protecting data can provide the peace of mind necessary to know your business can be back up and running.
- Protecting information in an isolated environment and using a physical or logical air gap to ensure data can’t be compromised
- Putting capabilities in place to automate recovery so panic doesn’t impede the recovery process and to ensure consistency, repeatability, and accuracy of the recovery process.
Keep in mind, it doesn’t matter what data you have or where it lives for any of these best practices. Data can be on physical devices, in virtual machines or in containers and can live on prem or in the cloud, these best practices apply and are the same.
Together i-Virtualize and IBM can help you ensure your business is ready for anything. Ask us about our cyber resilience assessment today.
Want to learn more about cyber resilience best practices? Watch Kosta’s presentation to learn more about how to strengthen your resolve and resilience.